An introduction to Symbiotic's restaking marketplace
Useful Links
-
Website: https://symbiotic.fi/
-
Documentation: Protocol Docs | GitHub | Audits
-
Contracts: Contract Deployments
-
Dashboard: Symbiotic Deposits Dune Dash
#Introduction
Symbiotic is a generalized shared security protocol that serves as a coordination layer between networks (demand for economic security) and restakers (economic security suppliers). The protocol is designed to be highly flexible and modular, allowing networks to customize their staking processes and opt in and out of shared security arrangements, tailoring the protocol to fit their specific needs. Additionally, the multi-asset and network-agnostic design supports scalable and capital-efficient sourcing of economic security, enabling more efficient use of capital across networks.
Symbiotic recently became a competitor among restaking marketplaces with its mainnet deployment in June 2024. Its primary value propositions against the incumbent, EigenLayer, are its agnostic stance on restaked collateral types and preference for permissionless network customizability that intends to improve competition and decentralization. By offering a neutral coordination framework and new primitives for modular scaling, it gives networks the autonomy to decide how to implement staking, including how to handle rewards, slashing, resolution mechanisms, asset ratios, collateral assets, and node operator selection. The protocol is built on non-upgradeable core contracts on Ethereum to minimize external governance risks and single points of failure, ensuring risk minimization through immutability.
Symbiotic launched its devnet on August 12 and plans to launch the full, immutable protocol in Q3.
#Section 1: Value Proposition and Adoption
This section will include an overview of Symbiotic's design goals and unique value proposition, especially how it relates to competing restaking marketplaces. It will also cover adoption metrics, its partnership ecosystem, and growth initiatives, such as through establishment of a points program.
#1.1 Symbiotic Key Features
Capital Optimization
Symbiotic maximizes capital efficiency through an innovative approach to node operator onboarding. By implementing an operator-centric cross-network framework, Symbiotic enables operators to connect across multiple networks simultaneously and significantly improve overall network capital efficiency.
Modularity
The protocol employs a minimal coordination layer, allowing integration with both existing and future network structures. This modular design ensures Symbiotic's compatibility with a wide range of crypto projects in the market, enhancing its versatility and adaptability.
Permissionless
Symbiotic's core contracts on Ethereum are non-upgradeable, providing users with full control over shared security agreements. Smart contracts design mitigates governance risks, execution layer errors, and potential third-party interventions, enhancing the protocol's security and trustlessness.
Flexibility
Networks leveraging Symbiotic can customize various critical elements, including reward and slashing mechanisms, (re)staking processes, collateral assets, and node operator set selection criteria.
#1.2 Competitive Landscape
Symbiotic has some similarities and some differences between other restaking networks, primarily EigenLayer and Karak. While other restaking networks exist such as Nektar and Jito, their prelaunch nature makes comparison of limited utility.
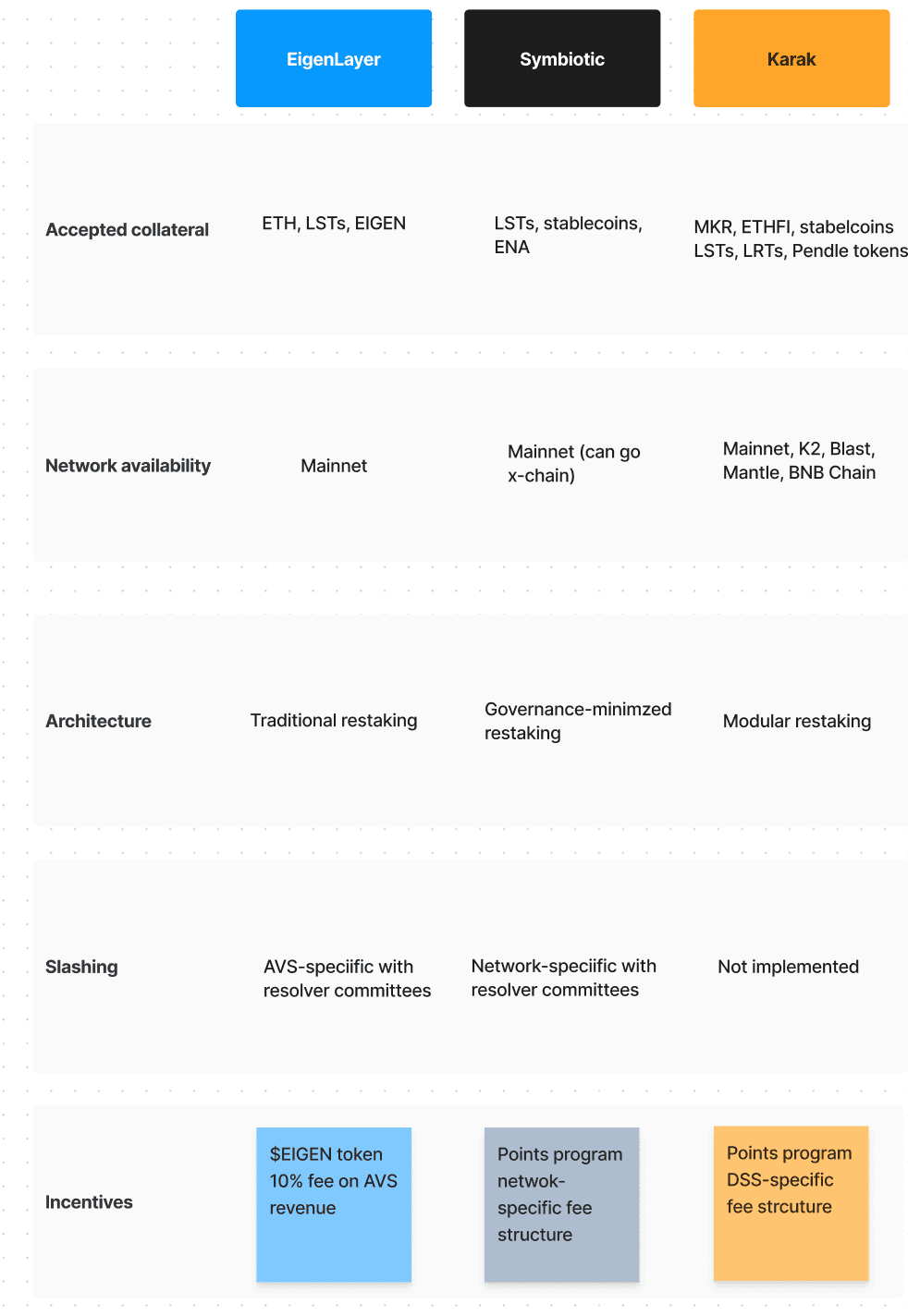
Symbiotic is only available on Ethereum mainnet, though it may operate multichain. This is in contrast to EigenLayer, who are exclusively restaking on mainnet. Karak operates on Mainnet, Blast, K2 (a Karak-specific L2), Mantle, BNB Chain and Mantle.
EigenLayer, the first to enter the restaking paradigm, has a much higher TVL ($15.5B) than Symbiotic’s $1.4B. Karak has $1B in TVL. It is worth noting that EigenLayer is currently experiencing a relative downtrend in TVL, having lost $2.5B in the last months. It is also worth noting that Symbiotic’s TVL jumped massively on July 4th, thanks to deposit caps being raised. The protocol is currently at its deposit limit, potentially indicating unmet demand for restaking on Symbiotic.
As a more DeFi-native restaking protocol, Symbiotic has enabled not only LSTs as collateral (such as wstETH, its largest deposit) but also stablecoins and select ERC20s, like Ethena’s governance token ENA or Frax Share (FXS). Symbiotic recently allowed the restaking of Bitcoin DeFi assets such as WBTC and tBTC. EigenLayer initially only accepted naked and staked Ether as collateral as well as the EIGEN token. This will change in the near future to allow all tokens. Karak similarly accepts a wide selection of assets including LP tokens, liquid restaked tokens, Pendle tokens, stablecoins and WBTC. Symbiotic is a middle-ground in this realm of accepted collateral.
Architecturally, Symbiotic is more modular than EigenLayer. Karak is also relatively modular, though Symbiotic has gone to great lengths to minimize governance and maximize programmatic operation.
In slashing terms, Symbiotic and EigenLayer use preconfigured AVS/network-specific slashing terms with instances potentially contested by committees or resolvers. Karak has not yet implemented slashing, though this is being worked on. Documentation indicates a similar resolver system.
Finally, operator income streams on EigenLayer are fixed at 10% of AVS revenue, whereas Symbiotic operator rewards are based on calculations detailed later in this report in Section 2.4. Karak’s DSSs split revenue with operators too. EigenLayer’s token is already live and is used to further incentivize AVS operation. While expected, details about Symbiotic and Karak tokens are thin, though points programs exist for both.
#1.3 Adoption Metrics
Since enabling collateral deposits in June, Symbiotic protocol has passed $1.4b in TVL ($1,462,000,000 - 15-08-2024). Below is the TVL collateral assets structure, showcasing a large proportion of stETH and the noteworthy inclusion of non-ETH collateral types, ENA and sUSDe:
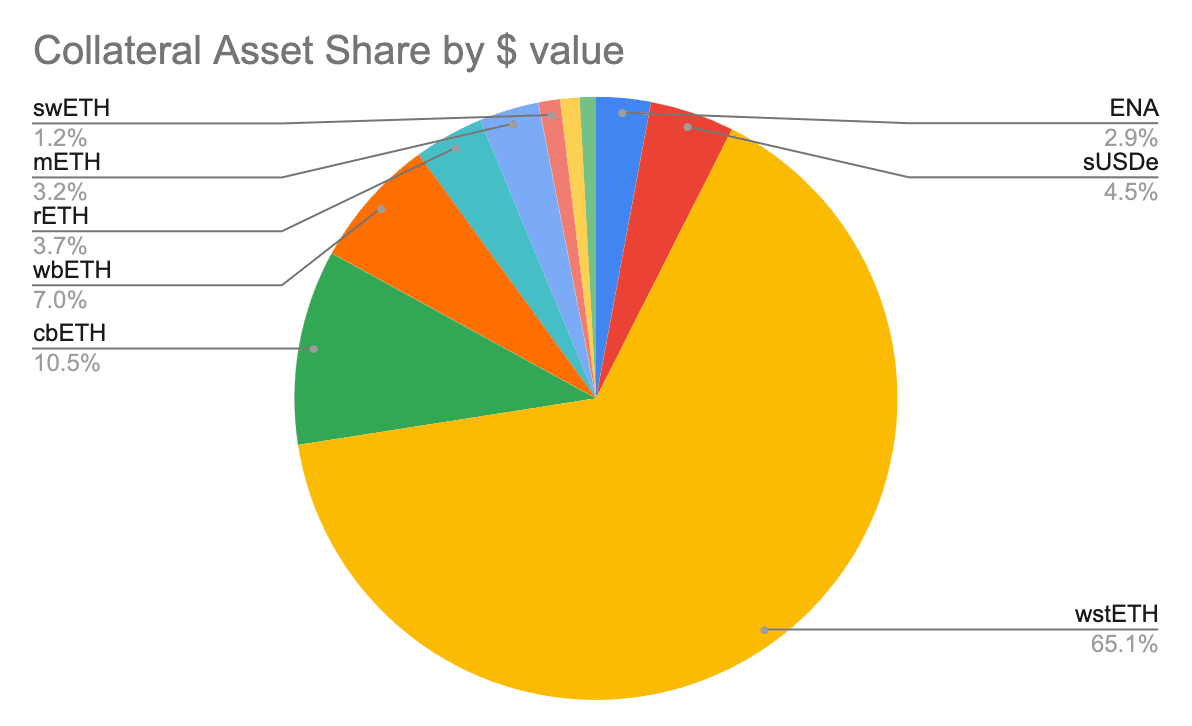
Source: Dune Analytics | Date: 8/14/2024
Since June 26th, there has been a noticeable increase in the number of new depositors. A portion of these addresses have made subsequent deposits, although the daily count of these repeat deposits remains relatively low in comparison to the influx of newcomers.
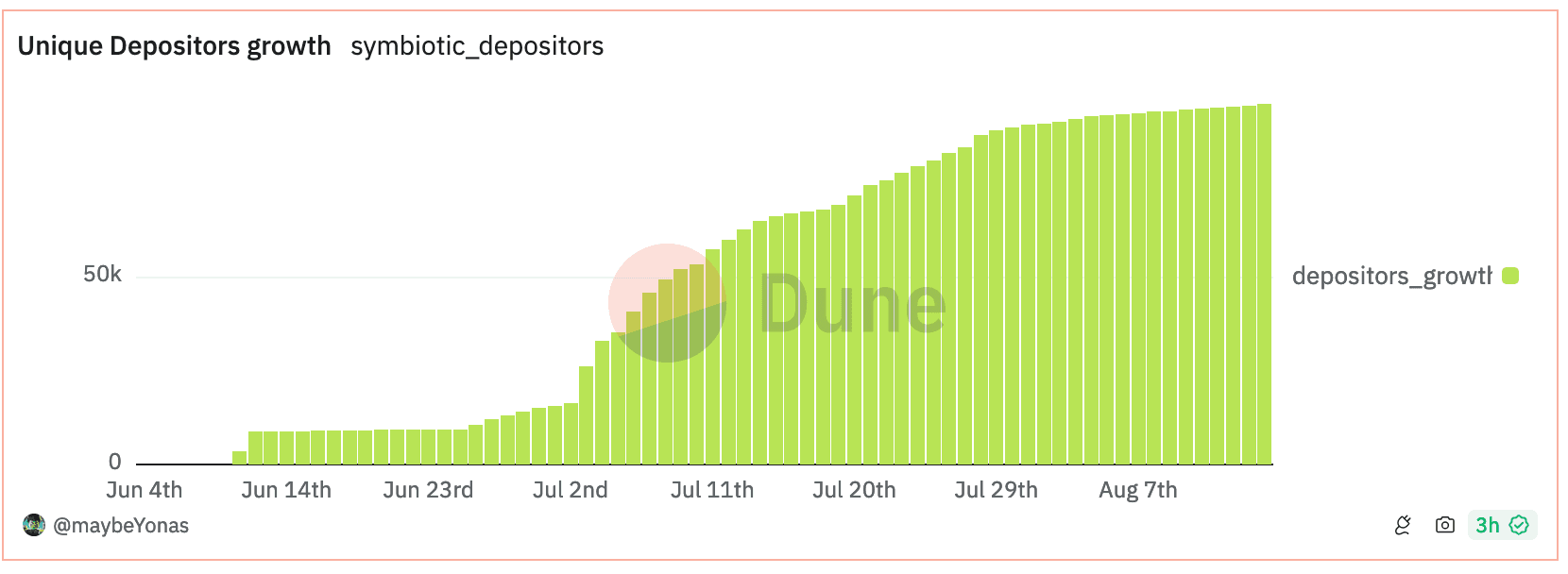
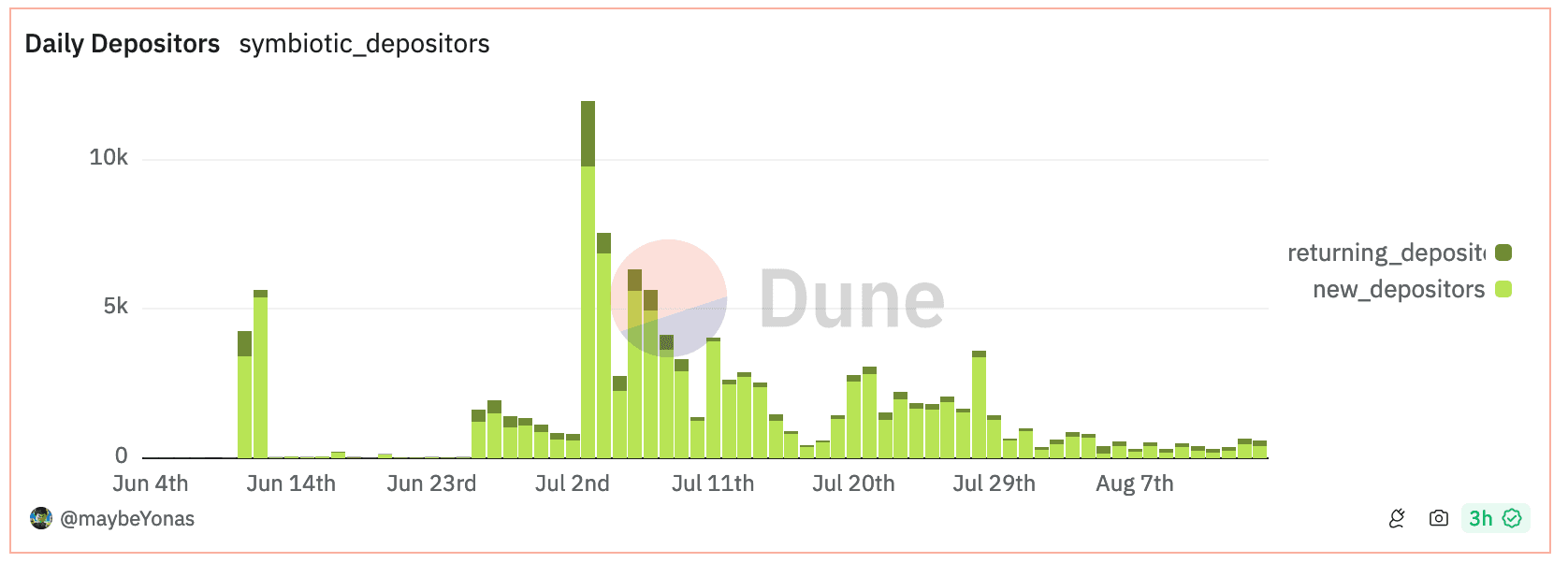
Source: Dune Analytics
#1.4 Ecosystem
On June 10, 2024, the Symbiotic team announced a fundraise of $5.8 million in seed round, co-led by Paradigm VC and Cyber Fund.
Lido’s involvement in the Symbiotic ecosystem has facilitated partnerships with other prominent LRTs, further expanding Symbiotic's reach and impact within the DeFi ecosystem. Additionally, Symbiotic collaborates with teams like Drosera to enhance application security on Layer-2 Ethereum through its restaking approach. Partnerships with Marlin Protocol's Kalypso further strengthen decentralized network security, underscoring Symbiotic's commitment to building a robust and secure DeFi infrastructure.
Symbiotic current partnerships:
-
Symbiotic integration into the LayerZero DVN framework via Ethena Labs (source 1) (source 2)
-
Ethena Restaking pools are live on Symbiotic (source)
-
Symbiotic Protocol has entered into a partnership with Marlin Protocol's ZK-proof market, Kalypso.
-
Symbiotic Partner and Mind Network entered into partnership to launch FHE shared security service based on restaking.
-
Symbiotic restaking infrastructure will use Bolt protocol, a protocol that enables Ethereum block proposers to make credible commitments, such as trustless pre-confirmations. Bolt protocol is built by Chainbound.
-
Stork network (oracle protocol) - announcement
-
Aori is looking to integrate Symbiotic restaking with stablecoin assets to hold market makers and solvers accountable when interacting with their high-frequency orderbook protocol.
-
Cycle Network is a blockchain-agnostic, unified liquidity network that will use Symbiotic to power its shared sequencer. (source)
-
A large number of DeFi applications have joined Symbiotic's first partner cohort including Frax, Redstone, EtherFi, Stide, Ditto, Router, Pragma and RollLeaf amongst others.
-
There are many other protocols preparing integration with Symbiotic for various use cases, from enhancing economic security to decentralizing oracle networks and facilitating sovereign rollups. Some of those protocols are Fairblock, Aori, Drosera, Ojo, Blockless, Rollkit, Aizel, Mind Network and DOPP.
#1.5 Points Program
The Symbiotic Points program is outlined in Section 1.9 of the Terms of Use. As per its provisions, the points serve as a reward mechanism for users who interact with the Symbiotic front-end and protocol, yet they hold no intrinsic cash or monetary value. Users should note that these points cannot be converted into cash or any form of currency.
Participation in the points program signifies the user’s acceptance of the program's terms as stipulated at the time of use. Importantly, the company operating the front-end retains the exclusive authority to modify these terms. It is crucial for users to understand that there is no guarantee or entitlement to a minimum accrual of points. The design of the points system, as an optional enhancement, aims to encourage user engagement rather than serve as a form of compensation or remuneration for services.
The company reserves the right to cancel or revoke points at any time under specific circumstances. These include breaches of the Terms of Use, abuse of the points program, or involvement in any fraudulent activities.
#1.6 Potential Use Cases
Symbiotic is a highly promising technology with a variety of potential use cases. With the preface that these use cases are possible but not yet delivered, Symbiotic restakers could look forward to helping advance a variety of fields:
RWA asset tokenization
Real world assets (RWAs) are onchain representations of financial or physical assets that could use restaking to clearly detail ownership. Symbiotic could use pooled security to prevent double-spending and prevent tampering with property transfer - something critical for an onchain asset with its value held off-chain.
Decentralized Social Media platforms
Social media platforms can provide users with greater control over content and resist censorship by using Symbiotic. They may for example only allow content to be hosted with nodes that have restaked their ETH, which have certain prerequisite moderation rules hardcoded. Slashing mechanisms may also help reduce spam or misinformation, providing a meaningful improvement over traditional social media networks.
Decentralized Content Sharing platforms
Decentralized content sharing platforms may use Symbiotic restaked assets to allow users to share content without relying on centralized networks thanks to economic incentives. These income streams could incentivize traditionally expensive operations such as maintaining content integrity and reliable access while penalizing actors that compromise data through slashing.
Crypto Gambling platforms
Symbiotic restaking can improve the trust and fairness of crypto gambling platforms by securing the underlying smart contracts that manage wagers and payouts. Validators with restaked ETH could ensure that all bets and results are accurately recorded on the blockchain, with slashing penalties for any dishonest behavior. This builds user confidence, knowing that the outcomes are genuinely random and the platform is secure against fraud - a significant value proposition compared to centralized sites.
Blockchain Gaming platforms
Symbiotic could secure smart contracts and NFTs used in blockchain games, ensuring that player transactions and asset ownership are immutable. Restaked ETH could back the game transaction layer where players buy, sell or exchange in-game assets, ensuring that all trades are fair and final with slashing mechanisms to prevent cheating. This presents a reduced overhead for games looking to run their own chains, which have so far faced significant difficulties.
Developer framework for chain-agnostic (network-neutral) dapps
Symbiotic could enable a unified security layer for dApps that operate across different blockchains. A developer building a chain-agnostic dApp could use restaked ETH to secure transactions on multiple chains simultaneously, letting the dApp operate securely regardless of the underlying blockchain. This reduces the complexity and cost of maintaining separate security measures for each chain, while also enhancing the dApp's reliability and trustworthiness.
Indeed, this may be the most compelling use case for restaking protocols. Network neutrality is a significant value-add to blockchain application development.
Blockchain Analytics platforms
Symbiotic could enhance security for blockchain analytics platforms by ensuring that underlying data is accurate by using restaked ETH to secure the smart contracts that collect and process on-chain data, guaranteeing correct results. Additionally, coprocessors built into smart contracts could be secured by restaking, ensuring that any computations performed onchain are both correct and tamper-proof.
Open AI networks and Agents
Symbiotic could incentivize AI networks, which require a high level of computational accuracy, data security and tamper-resistant environments to function effectively. Restaked assets could provide the necessary market mechanism to keep these networks / agents online and slashing conditions could act as an effective disincentive to the often-cited issue of LLMs "inventing" facts.
Other use cases
Symbiotic could also provide the necessary infrastructure for privacy networks, decentralized API (RPC node providers), data marketplaces, public goods and donation platforms and much more. These have traditionally been difficult to incentivize economically and Symbiotic restaked assets could provide both the incentive and disincentive they have been missing to sustain their operation in an honest manner.
#Section 2: System Architecture
This section will offer information that is currently known about Symbiotic's system architecture, given the relatively early stage of development. Known information includes the Symbiotic code repositories, deployed contracts, and documentation. Although all features are not currently live, the Symbiotic team has outlined system architectures for features such as core system components, slashing, and rewards handling.
#2.1 Smart Contracts
Symbiotic protocol smart contract architecture:
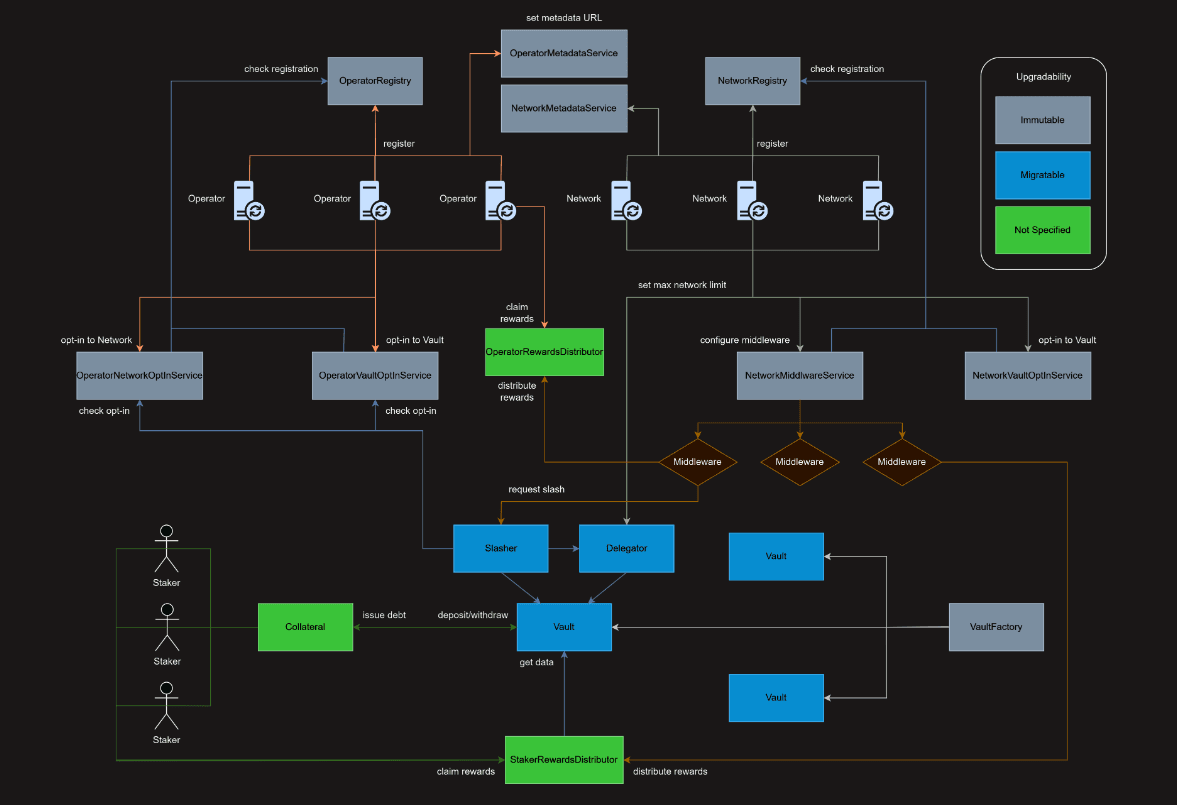
Source: Symbiotic documentation
Note that, as of the date of this writing, only the DefaultCollateral contracts have been deployed, but all contracts are published on the Symbiotic GitHub repository. On Symbiotic's GitHub, smart contracts are set up in 3 repositories: "collateral", "core" and "rewards".
It is critically important to underline that the functions referenced in later sections concerning slashing mechanics and reward distribution (section 2.3 and 2.4) are presently conceptual as detailed in the documentation and have not yet been implemented. The same status applies to the DefaultRewardDistributor and IRewardsDistributor contracts, which have not been deployed yet.
There are two published audits of the deployed contracts by reputable auditing firms:
-
StateMind Аudit (DefaultCollateral contracts)
-
ChainSecurity Audit (DefaultCollateral contracts)
The GitHub repos core and rewards both indicate that audits are in progress for these repos and are under active development.
A detailed compilation of contract functionality in these repos can be referenced here.
#2.2 Core Components
The Symbiotic protocol comprises five core components that work together to ensure robust security and decentralization.
-
Collateral refers to assets locked within the system to guarantee network security and stake-backed assurances.
-
Vaults are secure storage units where collateral is held and managed.
-
Operators are entities responsible for maintaining network operations, staking collateral, and ensuring reliability.
-
Resolvers play a crucial role in resolving disputes and verifying network activities, providing an additional layer of security.
-
Networks are the ecosystems that integrate with the Symbiotic protocol, leveraging its security and coordination features to enhance their own decentralization and efficiency.
Each of these components will be explained in detail in the rest of this report.
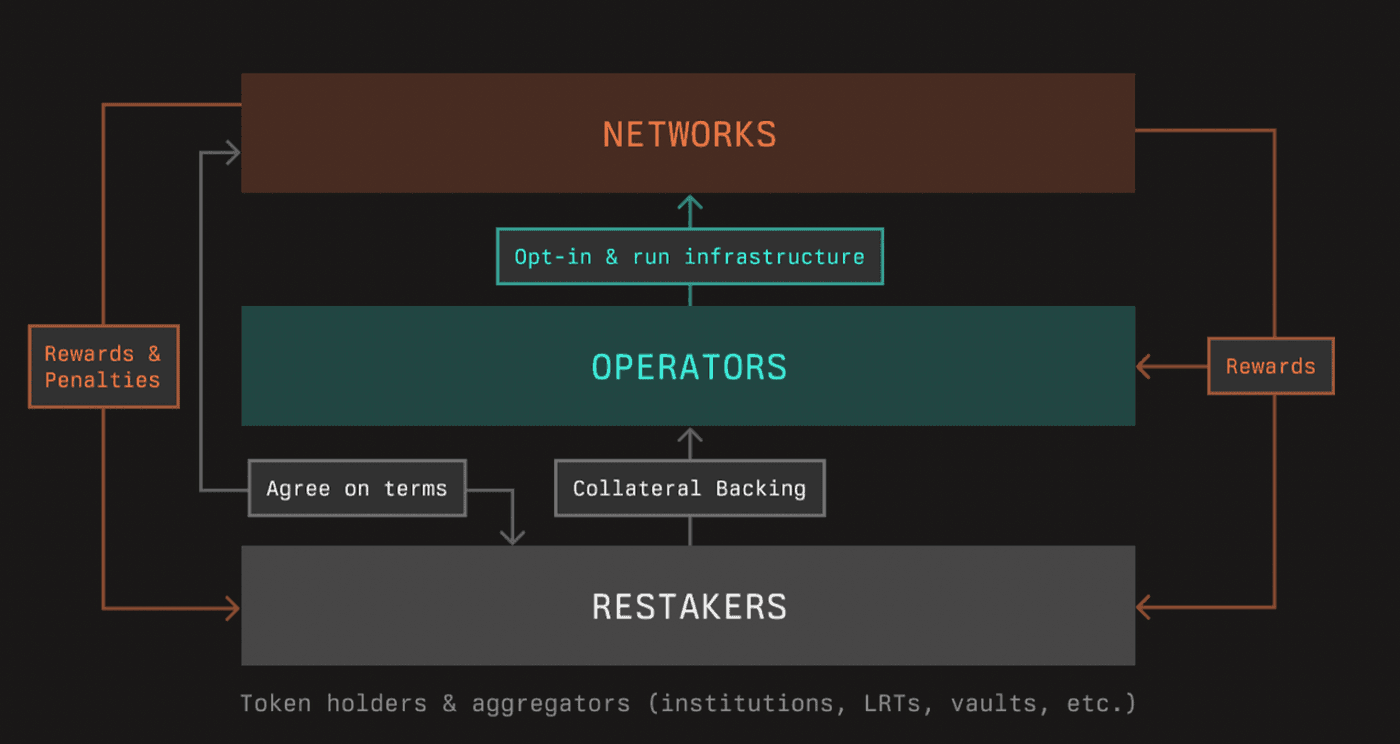
Source: Symbiotic documentation
#2.2.1 Collateral
Collateral serves as the security layer within the ecosystem, representing underlying on-chain assets. This collateral can encompass a variety of assets, including ERC20 tokens, Ethereum validator withdrawal credentials, and other on-chain assets, regardless of the specific blockchain they reside on.
Symbiotic allows users to hold restaked assets outside of the Symbiotic protocol (i.e., in a DeFi position on other networks). This is achieved by creating a tokenized representation of the collateral position (underlying asset), which separates slashing ability from the underlying asset itself. Tokenized collateral positions in Symbiotic are ERC-20 tokens with extended functionality to handle penalties.
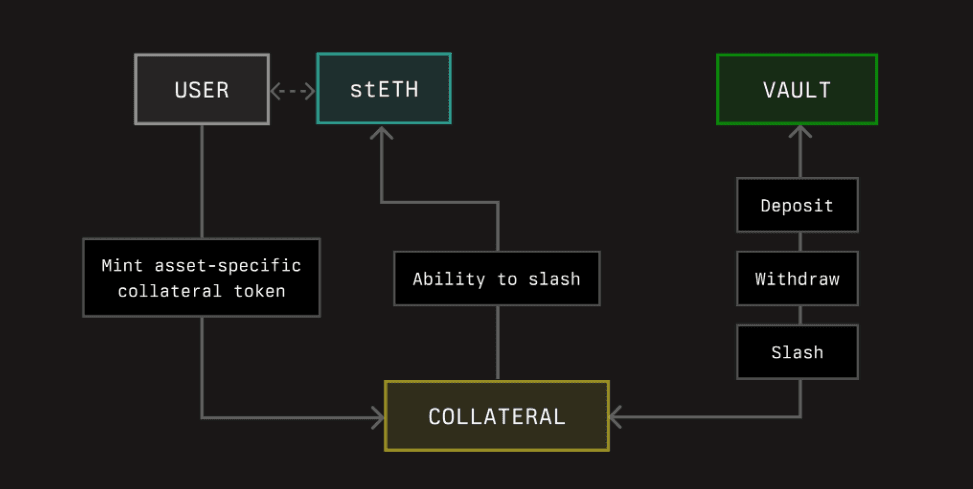
Source: Symbiotic documentation
Collateral contracts deployed on mainnet, as of July 2024:
Source: Symbiotic documentation
Note: Default Collateral is a wrapped version of the internal asset token.
#2.2.2 Vaults
Vaults in the Symbiotic protocol serve as the delegation and restaking management layer. They handle essential processes such as accounting, delegation strategies, and reward distribution. Vaults are configurable and can be deployed in an immutable, pre-configured manner or with an owner who can update vault parameters. They are intended for use by operators and curators, such as crypto institutions or liquid (re)staking protocols, to create differentiated products.
Vaults manage deposits, withdrawals, and slashing of collaterals. They define and implement delegation and restaking strategies to operators across Symbiotic networks. Additionally, vaults distribute staking rewards from networks to collateral depositors.
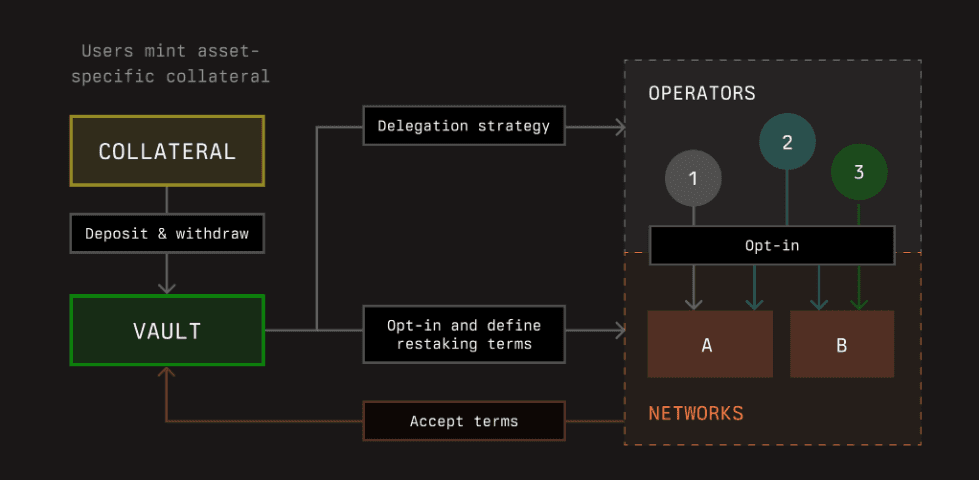
Source: Symbiotic documentation
Below are descriptions of the three functions of Vaults:
-
Accounting
-
Delegation Strategies
-
Reward Distribution
#1. Accounting
Vaults in the Symbiotic protocol handle several critical accounting functions:
-
Deposits: Any holder of the collateral token can deposit it into the vault using the deposit() method. The user receives shares in return, and the deposit instantly increases the active balance of the vault.
-
Withdrawals: Depositors can withdraw their funds using the withdraw() method, which involves a request and claim process. The user requests the withdrawal at the current epoch and can claim it when the next epoch ends. The withdrawal delay varies from one epoch to two epochs. Withdrawn funds are immediately reduced from the active balance but remain slashable until the next epoch ends.
-
Slashing Mechanics: Vaults provide strict guarantees regarding slashing to networks and stakers. At the beginning of each epoch, the network captures the state from vaults and their stake amount, ensuring slashing guarantees for the entire epoch. If a slashing incident occurs, the network has at least one epoch to request, veto, and execute the slash.
-
Epochs: Epochs are consecutive and have a constant size defined at deployment. The total supply of collateral is the sum of the active balance and the balances of the current and next epochs.
#2. Delegation Strategies
Vaults allow deployers or owners to define and implement various delegation and restaking strategies. These strategies can be customized based on the needs of operators and curators.
-
Operator-Specific Vaults: Operators can create vaults with collateral restaked to their infrastructure across different network configurations. Multiple vaults with varying configurations can be created to service clients without additional node infrastructure.
-
Curated Multi-Operator Vaults: Curated configurations of restaked networks and delegation strategies to a diversified set of operators. Custom slashing limits can be set to cap the collateral amount that can be slashed for specific operators or networks. Networks must accept the terms of these commitments for the vaults to provide their curation.
-
Immutable Pre-Configured Vaults: Vaults can be deployed with pre-configured rules that cannot be updated to provide extra protection for users. This setup is suitable for users who are not comfortable with the risks associated with changing vault configurations.
#3. Reward Distribution
Vaults in the Symbiotic protocol are responsible for distributing staking rewards from networks to collateral depositors.
-
Reward Mechanism: Rewards within the vault can be in different tokens, even though all operations and accounting are performed with the collateral token. Funds are represented internally in shares, but external interactions are done in absolute amounts of funds.
-
Reward Distribution Process: The vaults distribute rewards based on the shares held by depositors. The distribution mechanism ensures that rewards are fairly allocated according to the proportion of shares held by each depositor.
In summary, vaults in the Symbiotic protocol are a versatile and essential component, managing key processes such as accounting, delegation strategies, and reward distribution. They provide a flexible and secure framework for operators and curators to create customized staking and restaking products, ensuring the efficient operation of the Symbiotic economy.
#2.2.3 Networks
Networks are decentralized ecosystems that leverage the protocol's security and coordination features to enhance their own decentralization and efficiency. These networks can define and adapt their methods for onboarding, incentivizing, and penalizing operators and their delegators, tailoring their operations to the specific needs of their ecosystem. By integrating with Symbiotic, networks gain access to a flexible and secure restaking framework that allows them to scale and optimize their security in a decentralized manner.
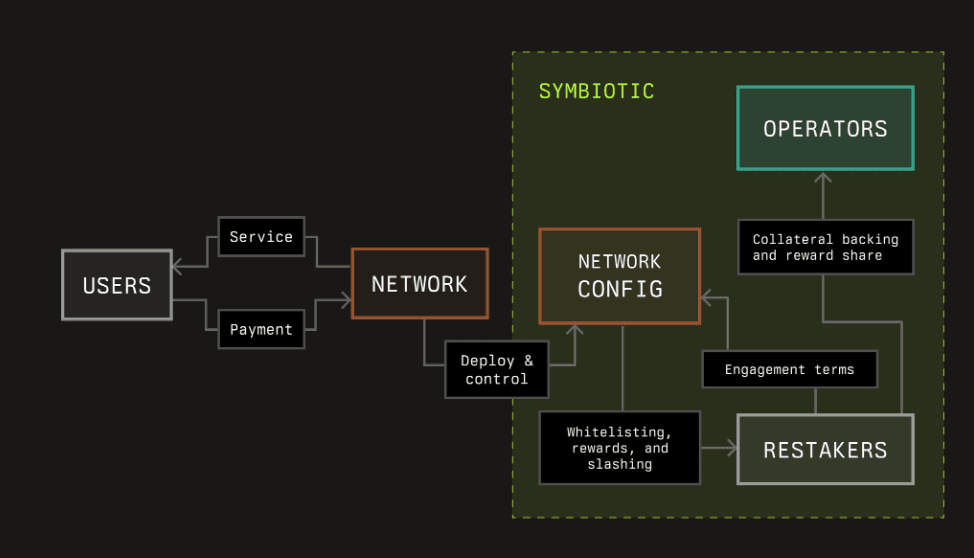
Source: Symbiotic documentation
The following features enable Networks to leverage the full potential of Symbiotic protocol:
-
Decentralized Services: Networks use Symbiotic to facilitate trust-minimized services by utilizing a distributed set of node operators.
-
Customization: Each network can adapt its methods for onboarding, incentivizing, and penalizing operators to fit its unique needs, ensuring optimal operation and security.
In Symbiotic, Network business logic consists of two parts:
-
Middleware Contract: the business logic part responsible for assembling the operator set and staking/slashing/reward distribution. Symbiotic does not specify the exact mechanic/implementation. It only provides interfaces on how middleware can interact with the core part of the system.
-
Network Address: an EOA or contract serving as the gateway to deploy and manage the Middleware Contract and as the infrastructure network delivering a service to users.
#2.2.4 Operators
Operators are the entities responsible for running the infrastructure required by networks. They can opt into different networks and receive economic backing from restakers through vaults, facilitating the essential operational activities of the network.
Operators run infrastructure for decentralized networks within and outside the Symbiotic ecosystem. The protocol creates a registry of operators, logs interactions with the protocol, and protocol participants can attach credentials and other data to operator entities. In the initial version, this includes metadata about operator entities provided by the operators themselves, and data from their interactions with the Symbiotic protocol (source):
-
Networks that the operator opted into and associated cryptographic keys
-
Associated vaults and restaked collateral from vaults
-
Historical logs of slashings and all other interactions with the Symbiotic ecosystem
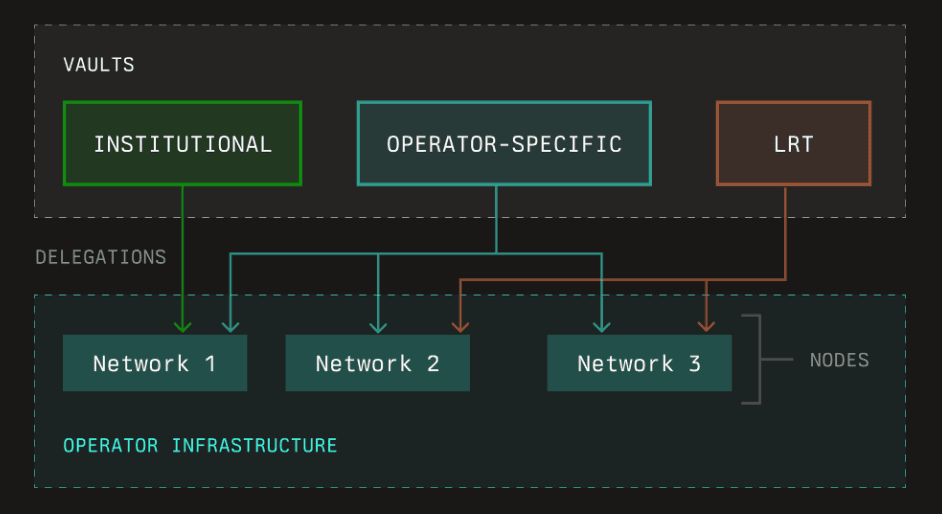
Source: Symbiotic documentation
Operators' key responsibilities are:
-
Infrastructure Management: Operators run the necessary infrastructure for decentralized networks both within and outside the Symbiotic ecosystem. This involves managing nodes and ensuring the seamless operation of the network.
-
Economic Backing: Operators receive economic support from restakers, enabling them to fulfill their roles effectively. This financial backing helps operators maintain and scale their infrastructure to meet network demands.
-
Networks selection (AVS selection): Operators can opt-in to a network, and may be included in the validator set depending on factors specified by the network such as reputation or stake amount.
#2.2.5 Resolvers
Resolvers are entities or contracts tasked with managing slashing penalties for operators. They have the authority to pass or veto penalties and can be automated or consist of entities like slashing committees. Resolvers play a crucial role in maintaining the integrity and security of the network by arbitrating penalties, ensuring that operators adhere to performance and security standards.
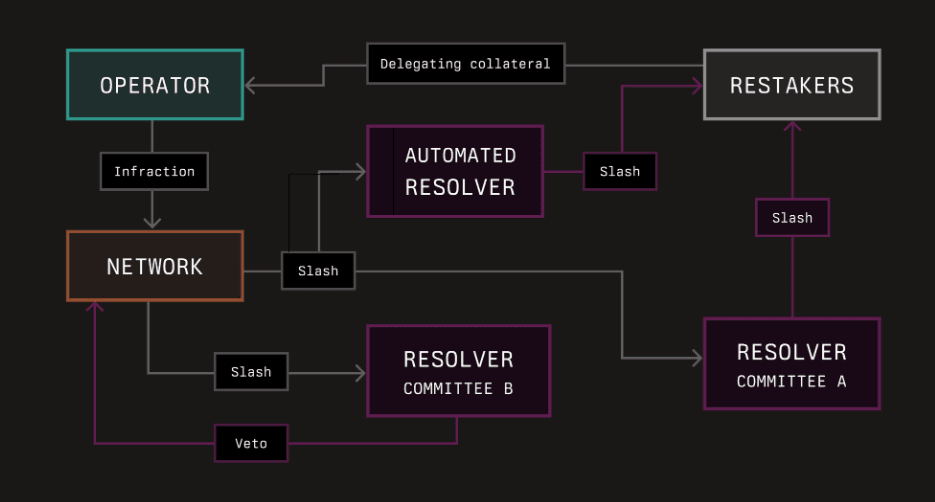
Source: Symbiotic documentation
Resolvers are in general responsible for:
-
Penalty Management: Resolvers are responsible for executing or vetoing slashing penalties based on operator performance and security adherence.
-
Dispute Resolution: Provide an additional layer of security by resolving disputes and verifying network activities, ensuring fair and accurate enforcement of penalties.
#2.3 Slashing
In Symbiotic, slashing serves as a mechanism to penalize operators who fail to meet established performance or security standards. The process involves reducing the collateral of these operators as a consequence of their infractions. Slashing can occur under various conditions, including performance failures, security breaches, and protocol violations. Performance failures might include not meeting uptime requirements or processing transactions incorrectly, while security breaches involve actions or inactions that compromise network security. Protocol violations are any breaches of the network’s rules and regulations.
#Role of Resolvers
Resolvers are primarily responsible for executing slashing actions. These can be automated systems that trigger slashing based on objective infractions, such as downtime or incorrect block proposals, or slashing committees that make decisions based on more complex or subjective criteria. Additionally, external dispute resolution frameworks may handle disputes and determine the appropriateness of slashing actions. Network builders also play a role by defining slashing criteria and collaborating with resolvers to ensure alignment with the network’s security and performance requirements.
Certain resolvers have the authority to override initial slashing decisions. This may occur if the initial decision was erroneous, new evidence emerges, or an appeal process within the slashing committee or an external dispute resolution framework deems the slashing inappropriate. In some cases, vault participants, such as restakers or operators, might have mechanisms to collectively vote on or appeal slashing decisions, depending on the specific governance structures of the vault.
#Is Slashing Live?
The live status of slashing mechanisms within the Symbiotic protocol depends on specific implementations and activations by network builders. While the protocol provides the necessary infrastructure and guidelines for slashing, actual enforcement and activation are contingent upon the readiness and adoption by individual networks.
#Slashing Process
Symbiotic employs an epoch-based system, which is fundamental to managing withdrawals and slashing processes. This system provides a structured timeline for operations within the protocol, ensuring predictability and synchronization. Epochs follow each other without gaps, and the duration of each epoch is fixed at deployment. The ongoing epoch is referred to as epoch. Requests made in epoch become claimable in epoch + 1, creating a variable withdrawal delay between EPOCH + 1 and 2 * EPOCH. This system provides predictable timeframes for protocol operations, ensures synchronization across the network, and allows for controlled release of funds, enhancing security.
The protocol implements a three-step slashing process to ensure fairness and security:
-
request to slash (
**requestSlash()**): initiate the slashing process without immediately applying the slash. -
optional veto slash (
**vetoSlash()**): allows for intervention to prevent unjust slashing, performed by a designated resolver. -
execute slash (
**executeSlash()**): finalizes and applies the slash if not vetoed, and this can be executed by any party after the veto phase.
Each slash request has an executeDeadline, and successful slashing reduces the limits of both the slashed operator and the requesting network. The veto phase provides a crucial check against erroneous or malicious slash requests.
#Slashing Modalities
Slashing is subject to specific limitations at both the operator-network and network-resolver levels.
The operator-network limit defines the maximum amount of funds that can be slashed upon a network's request to slash a particular operator. Through this procedural control, the slashing limits remain flexible and can be adapted based on the network's operational requirements. The limitation is tailored to each operator-network pair and can be adjusted by OPERATOR_NETWORK_LIMIT_SET_ROLE holder via the operatorNetworkLimit() method.
The network-resolver limit exemplifies hierarchical control mechanisms that dictate the maximum funds that can be slashed when a network requests such action with a specific resolver. This limit is also unique to each network-resolver pair and can be altered by the NETWORK_RESOLVER_LIMIT_SET_ROLE holder using the networkResolverLimit() method. It also allows for setting an upper threshold of the slashing through the maxNetworkResolverLimit() function.
Modifications to these slashing limits take effect differently based on the action: decreases are implemented after the conclusion of the current epoch plus one, while increases are enacted immediately.
It is noteworthy that the actual slashed amount can be less than the initially requested amount. This discrepancy arises from the dynamic nature of the aforementioned limits, which can be adjusted between the time a slashing request is made and its actual execution. Such variability ensures that the slashing process remains fair and responsive to changing network conditions.
Importantly, only operators who have explicitly opted into a network or vault can be subjected to slashing. The opted-in status signifies an operator's agreement to participate and be bound by the network's rules. An operator cannot be slashed if they were not opted-in prior to the commencement of the preceding epoch which actually safeguards operators from retroactive penalties.
#2.4 Rewards
Staker rewards in Symbiotic vaults are crafted to remunerate participants who actively engage in staking their tokens. The rewards are allocated based on the proportion of active shares held by a staker at a specific timestamp in comparison to the aggregate total of active shares in the system.
The Vault provides key data necessary for reward calculations, including active shares held by each staker at given times and the total active shares across the system at those times. It also offers checkpointed getters for precise data retrieval. These elements are integral to the reward calculation as per the formula:

Rewards distribution is managed by external reward contracts. The DefaultRewardDistributor contract, which implements the IRewardsDistributor interface, encapsulates the logic required for distributing and claiming rewards. The function distributeReward(network, token, amount, timestamp) is executable only by whitelisted networks. The claimRewards(recipient, token, maxRewards, activeSharesOfHints) function allows any staker with accrued rewards to claim them.
Operator rewards, on the other hand, are designed to incentivize network operators based on their active participation and stake within the network. The Vault Contract oversees the operators' stakes and tracks their activities. By utilizing Vault.minStakeDuring(network, resolver, operator, duration) the Vault retrieves the minimum active stake of an operator over a specified duration.
The mechanism of reward distribution for operators is determined by the networks themselves. Rewards can be computed off-chain and distributed through batch transfers, or a Merkle tree could be generated to enable operators to claim their rewards independently. Additionally, rewards can be calculated on-chain within the network's middleware, offering flexibility in the reward distribution process.
Networks obtain staking information for each epoch from the Symbiotic system. Operators are required to register details, including commission rates and fixed payments. For on-chain calculations, the middleware leverages the obtained data and may invoke the minStakeDuring function to verify the stake during an epoch. This function is routinely called by operators or any entities needing to verify an operator's active stake.
#Are Rewards Available?
There is no specific mention of live rewards on the Symbiotic protocol. Codebase development and respective implementations on the operator side should be achieved first before making the reward system available.
#Conclusion
Symbiotic is distinguished by its permissionless and modular architecture, offering users considerable flexibility in staking their assets. By enabling their participation in restaking activities without requiring explicit permissions, the protocol streamlines user engagement and broadens adoption.
The support of multi-asset deposits of any ERC-20 token allows users to diversify their staking strategies beyond a single asset type. This versatility provides an advantage over the ETH-centric EigenLayer, but may also lead to the formation of riskier networks that rely on collateral assets with sub-par economic security assurances. Symbiotic’s emphasis on interoperability and collaboration with other protocols, such as leading LRTs, further enhances the overall user experience and expands the breadth of potential applications.
Epochs play a crucial role in the slashing process by providing a structured timeline for operations within Symbiotic protocol. Slashing is subject to specific constraints at both the operator-network and network-resolver levels. While the slashing mechanisms have been conceptualized and outlined, their actual implementation and activation are pending further protocol-level developments.
Similarly, the reward mechanisms designed to compensate stakers and operators are theoretically sound and have been developed to the codebase level. Despite the mathematical clarity and development progress, the launch of rewards distribution is yet to be scheduled within a definitive timeline, indicating the need for further preparations before this feature goes live.
Our initial impression of Symbiotic is that it has substantial potential to become a viable contender among restaking marketplaces, bearing in mind that the early stage of development precludes an authoritative course of action at this time. We recommend YieldNest monitor Symbiotic developments and consider increasing exposure to its ecosystem as the marketplace matures.
